TIPS & BEST PRACTICE 23. NOV 2022
What are email key pairs and certificates, and how are they used?
Companies dealing with email encryption and digital signatures will inevitably confront the issue of keys and certificates. This article briefly overviews the S/MIME certificate standard, which is widely used in the corporate world.
From public key to S/MIME certificate
- When you generate a key pair, you create a “private key” and a “public key.” The two keys form a fixed, mathematically dependent pair.
- The public key is signed with the corresponding private key and sent to a trust center.
- After predefined verification processes, the trust center signs the public key, thereby turning this key into an email certificate. In the certificate, the trust center is subsequently designated as the issuer.
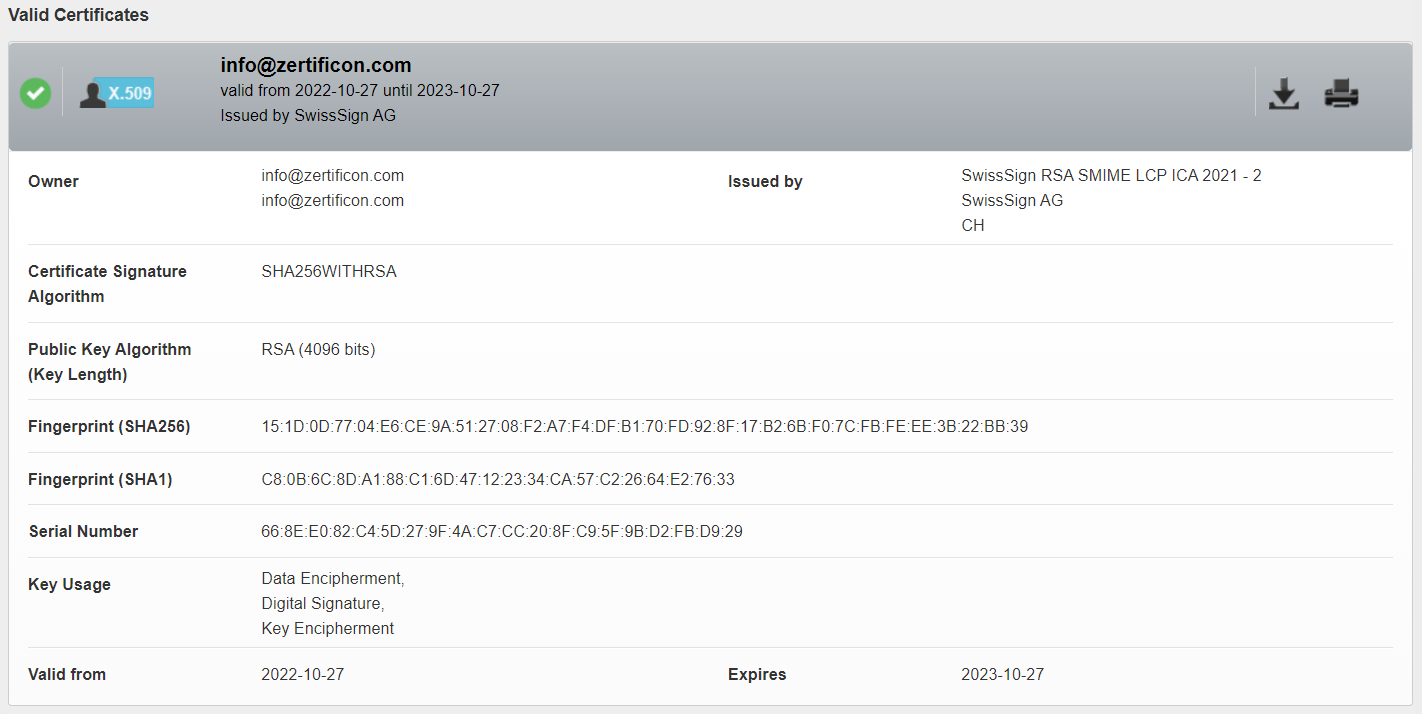 Details of an email certificate displayed in Z1 Global TrustPoint
Details of an email certificate displayed in Z1 Global TrustPoint
The functions of the private key and the certificate
By default, the private key has two functions and is used only by the owner of the key:- To digitally sign outgoing emails
- To decrypt incoming encrypted emails
- To verify the validity of your digital email signatures
- To encrypt emails sent to you
You cannot control the use of the certificate. Your scope of influence is limited to the private key! If you provide your communication partners with certificates for validating email signatures, you cannot prevent them from sending you encrypted emails.
In modern cryptography, signature and encryption are inseparable through a mathematical and logical dependency—even if you find some information somewhere on the Internet to the contrary. Read more on Why digital email signatures and encryption go hand in hand.
You can automate all key and certificate management processes with Z1 SecureMail Gateway. Employees not only won’t need to manage their private keys. Z1 SecureMail Gateway comfortably solves the distribution of your certificates and the search and validation of external certificates. Z1 SecureMail Gateway makes the entire certificate exchange process between you and your communication partners automatic and all invisible in the background.
Additionally, Z1 SecureMail Gateway gives you easily customizable rule sets. That way, you can effortlessly define when encryption and signing must happen for individual users, groups, or even on a company-wide level!
Start your request right now to learn more about the benefits of centrally managed email encryption: