LEGAL REQUIREMENTS 13. MAY 2022
The latest court ruling on the EU Trade Secrets Protection Act in Germany: Is TLS encryption for emails sufficient as a protective measure?

The European Union’s Trade Secret Directive of April 2016 states that trade secrets are only deemed secret when protected by reasonable steps to keep them secret (Art. 2 para. 1c).
Given that the directive is transposed differently in each EU country, how can businesses across the EU make sure “reasonable steps” are always in place? Eventually, success for any company depends, more often than not, on guarding the most critical information.
We offer insight into a recent ruling about the sufficiency of TLS in protecting trade secrets in Germany. And Beyond Germany, can companies in the European Union prevent leaving the fate of their economic well-being at the hands of jurisdictions and verdicts?The case
The Schleswig-Holstein Higher Regional Court recently ruled on whether TLS encryption is sufficient for email under the German Trade Secrets Act (GeschGehG) (6 U 39/21). In this case, appropriate protection for an Excel spreadsheet containing “cost information” was the subject of assessment under the Trade Secrets Act.
The data classification in the Excel spreadsheet was as such: it requires protection but not of the highest level. Moreover, the rationale behind the verdict contends that there was no basis to fear third parties could have been probing for the transmitted data. Therefore, TLS (Transport Layer Security) was considered sufficient in this case. But with TLS, unlike content encryption with S/MIME or OpenPGP, only the transport path between two servers is encrypted, not the content itself.
We explain why this verdict does not mean TLS adequately protects business secrets.Trade secrets classification
The reasoning for the judgment invokes, among other things, a three-part classification of trade secrets (BeckOK GeschGehG/Fuhlrott, § 2 para. 23; Köhler et al./Alexander, § 2 para. 56; Maaßen GRUR 2019, 352, 356):
- top-secret information, the “crown jewels,” the disclosure of which would threaten the existence of the company
- important information, the disclosure of which could cause a permanent economic disadvantage
- sensitive information, the exposure of which could cause a short-term economic disadvantage
Protection Levels for trade secrets
As a rough guideline, the following assessment can be derived from the recent case:
| Information protection levels | Evident direction of future jurisdiction |
|---|---|
| Top secret | TLS not sufficient |
| Important | TLS rather insufficient |
| Sensitive | / TLS sufficient depending on further considerations (company size, standard security measures, etc.) |
Managing directors’ liability under the EU Trade Secret Act remains a risk in the absence of content encryption
Given the threat status and liability risks related to compliance requirements under the Trade Secret Act, management should reflect on this ruling with all its implications. Internally, the managing director is personally liable to the company for fines or claims for damages that could have been avoided through proper management and observance of IT compliance (cf. GmbHG § 43 para. 2.)
The Trade Secret Act (GeschGehG) has only been in force since April 2019 and is, therefore, a relatively recent law. It is conceivable that the ever-increasing cyber threats will be taken into account to a greater extent in the future, not just in Germany but for related cases across the European Union.
Why TLS encryption for email does not protect against many threats
The Schleswig-Holstein Higher Regional Court lawsuit did not address mass data collection from email traffic via automated systems. However, it’s not news since the 2014 Snowden revelations that the threat of systematic espionage attacks is ubiquitous and should be considered when securing business communications. Nowadays, it would be naïve to assume that data pass unfiltered through a network. Eavesdroppers have different motivations, but valuable information always finds its audience. In times of war of aggression against Ukraine, cyberspace is also being reinforced.
TLS does not provide an effective defense against surveillance attacks because, at any point, it only protects the connection between two servers, not the data itself. The data passes through nodes unencrypted. And These nodes are systematically spied on. Unlike when surfing the Internet with TLS, no direct connection between the sender and recipient is established when sending emails. Emails are sent through an unclear route via various servers as nodes. Only the start and destination are clear, but whose servers, how many lie in between, and how securely they are protected remain unknown.
Therefore, you shouldn’t make the need to protect your trade secrets dependent only on a jurisdiction that might evaluate TLS as sufficient. To protect your data and appear trustworthy to your business partners, you should technically be able to offer content encryption in addition to TLS encryption, which is already a technical standard in secure business communication.
Content encryption for email is widely used in enterprises that have a Gateway
In many industries, especially those with international business relationships such as automotive, transportation, pharmaceuticals, FMCG, retail, and critical infrastructures (KRITIS), TLS is unacceptable as the sole protection means for secure email. Instead, certificate-based content encryption is used across the board and centrally controlled via secure email gateways. More than 25% of the Top 100 German companies with the highest turnover already trust Z1 SecureMail Gateway!

Learn how to protect personal data in email exchanges by attending one of our webinars with a product demo:
“Easy and central implementation of email encryption with Z1 SecureMail Gateway.”
Webinars are available in the German Language. Requests for product demos in the English Language are reviewed individually. Do not hesitate to send a query to our sales team!
Authenticity is also fundamental for trade secrets
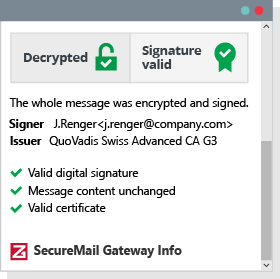 Test report in an email. You can trust this email!
Test report in an email. You can trust this email!
Entrepreneurs should definitely pay attention to emails’ authenticity to protect business secrets because data manipulation and fake sender identities are threats with high damage potential.
With just TLS protection, you can’t trust email content or even mail attachments. At the nodes that email takes on its journey from sender to recipient, any email can be intercepted, modified, and injected without the sender or recipient’s detection.
TLS also does not protect against CEO fraud and phishing. All of us receive fraudulent emails, and fake emails are getting better by the day—how many of you in Germany received emails on behalf of Postbank or Sparkasse that you did not send?
Z1 SecureMail Gateway provides a digital signature for emails to authenticate identities. No content has been altered when the signature is validated, and the sender is who he claims to be.
Recommendation for email protection levels for trade secrets
After explaining the weaknesses of TLS when it comes to protecting trade secrets, here is an overview of what level of protection would be appropriate. Our solutions ensure that the proper level of security is automatically maintained, depending on the classification. The gateway adjusts to recipients and invites them into encrypted communication with you, even if they do not have their own encryption technology.
| Information protection levels | Recommended encryption level |
|---|---|
| Top secret | Organizational End2End with gateway / Personal End2End all the way to the end device. Or Gateway encryption using particular BSI specifications |
| Important | Content encryption centrally controlled with gateway |
| Sensitive | Content encryption centrally controlled with gateway |
For a more comprehensive breakdown of email encryption via a gateway and end-to-end encryption up to the end device, check out this white paper: “End-to-end email encryption for enterprises.”
Security must be carefully thought through and consistently adapted to changing threats to drive digitalization forward. If you want to be able to do business tomorrow, you can’t afford to miss the boat on new technologies and security standards. Attend a webinar with a product demo, or get in touch directly. We are happy to advise you!